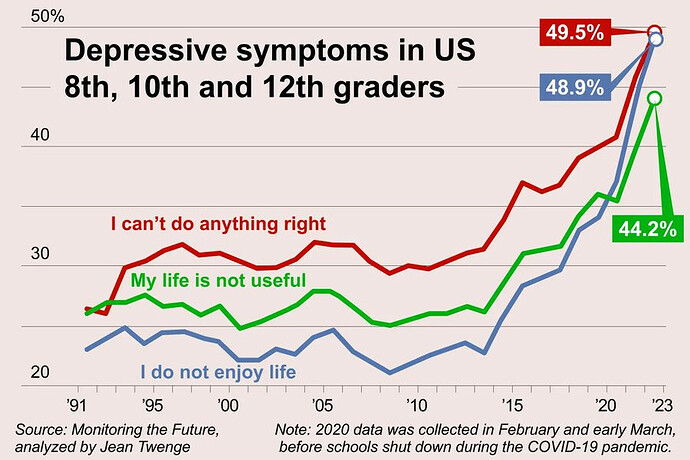
Starting with the March 2024 awards, movies will not be considered for a Best Picture nomination unless they meet two out of four standards.
One of them is featuring a lead or significant supporting character from an “underrepresented racial or ethnic group,” have a main storyline that focuses on an underrepresented group, or at least 30% of the cast comes from two or more underrepresented groups (women, ethnic minorities, LGBTQ or the disabled).
A full outline of the standards can be found on the Academy site.
⋮
“’All Quiet on the Western Front’ would not have been nominated,” said the director of the World War I film with a historically accurate white male cast.
“In terms of ‘Elvis,’ there are probably enough women and minorities to hit 30 percent and qualify,” Jim Piazza, co-author of “Academy Awards: The Complete Unofficial History,” told The Post. “But many of those people are in dance and party scenes and on-screen briefly. How they count will be difficult. There will be a lot of caveats.”
“Going further back, think about ‘Schindler’s List.’ Should that not have been nominated since there were no non-white people in the primary roles?” asked the director, referencing the 1993 Spielberg movie which largely features white male actors. “I’m wondering if Jewish people would count for ‘underrepresented racial or ethnic group,’ but it would be up to the Academy to figure that out.”
Other macho classics that, these days, would likely fall by the Best Picture wayside: “Gladiator” and “All the President’s Men.”
According to Newsweek, past nominees “Ford v Ferrari,” “Once Upon a Time in Hollywood,” “American Hustle” and “Joker” also would not have cleared the Best Picture bar.
Will this be the new way to “swat” people you don’t like – seems a plausible enough potential approach to disrupt or punish someone.
A stark reminder that whatever convenience these cloud based systems are thought to offer, it comes with a steep price.
How long before Alexa’s eavesdropping in one’s house may trigger political correctness thresholds that place the bad thinker on a list. Feels like social credit on steroids, implemented directly by the so-called private sector.
A service should only be removing content if they are legally liable for it, which they mostly aren’t under Section 230. In which case it’s the government’s fault for censoring it.
This is why letting your smart home be run by somebody else isn’t very smart. What’s next, Amazon or Apple or Google locking you out because Alexa hears something on the TV or radio that it misinterprets as not following the groupthink?
Or even more prosaic … Alexa overhears you speaking bad thoughts and promptly enforces the goodthink.
Why not to get the Alexa-connected bidet.
As the proud owner of a Toto Washlet (my best-ever purchase!), I am glad it has no (known) internet connection. BTW, I have just become aware of the dangers inherent in all my “smart” devices and IoT stuff. I am frantically trying to learn how to reconfigure my older modem or get a new one - so I can segment my network. I understand that, if the IoT stuff has a separate SSID, as on a VLAN or by other means as yet unknown by me, the threat is reduced or eliminated. I am having trouble finding a small enough IT consultant who will bother with a residential network. They all want businesses.
AI corporal punishment when you say the wrong thing in the can. That’s scary.
My wife has a fire tablet (she breaks a fair number of screens and they’re way cheaper than iThings). It took me a while to get it to quit responding to every Alexa request along with whatever echo was closest.
It isn’t so much as having a separate SSID (the name by which the Wi-Fi network is accessed) as being on a separate subnet within your local network (although assigning a different SSID may be part of setting up such a configuration). When setting up a system involving untrusted devices (either inherently untrusted, or because of the risk of their being infiltrated by malefactors due to security flaws), what you want to do is isolate them so they cannot be used as beachheads to attack machines on the same local network which contain sensitive data. Let’s assume your local network uses the commonly-used private IP range 192.168.0.0–192.168.255.255. You might assign your personal computers, network printers and storage devices, and mobile devices IP addresses in the range 192.168.0.1–255. These devices can all communicate freely with one another and establish connections to external sites on the Internet. You could then assign addresses from 192.168.1.1–255 to dodgy devices such as light bulbs, the refrigerator, trash mashers on the detention level, etc. If you have a separate firewall, it would be configured so devices on 192.168.0.x could connect to those on 192.168.1.x but those on the latter subnet could not initiate connections outside of their own subnet, and hence they wouldn’t be able to get to your trusted machines or external sites on the Internet. If you’re using services such as home security monitoring (for example, a site that checks whether your chest freezer is within its selected temperature range), you may need to open up limited Internet access to some devices on the IoT subnet, but often this is unnecessary.
With a dedicated firewall device, you can perform this partitioning on as fine grained a level as necessary and desired. With a modem/router, you usually have less flexibility in setting up such configurations.
As an example, at Fourmilab I have a local network subnet (LAN) on which the development machines and in house file and backup server communicate. These machines can connect to one another without restrictions. A separate network is the DMZ, on which machines accessible to the outside world via the Internet live (Web servers, data generators polled by outside sites, etc.). The DMZ machines can be accessed from the LAN for maintenance, but they cannot initiate connections to machines on the LAN, so even if one is broken into from outside, they cannot access or corrupt anything outside the DMZ. The DMZ machines are backed up to the backup server on the LAN and can be restored from it if they do suffer a break-in.
The Wi-Fi access points are configured with two SSIDs. The first is used by trusted mobile devices which are assigned addresses on the LAN subnet and have full access to the LAN. The second SSID is given to visitors. It assigns addresses from a “Guest” subnet. That subnet can initiate connections to the external Internet but cannot connect to either the LAN or the DMZ. This provides Internet access to visitors without exposing local machines to their depredations.
This is all implemented with my Check Point firewall, whose expense, gratuitous complexity, opaque documentation, and fragility I would not wish on my worst enemy. I have no experience setting up configurations like this on more human-compatible firewalls.
Pandemic response - particularly the protracted lockdowns - turned out be a massive own goal of epic proportions.
Very few people at the time questioned the rapid lemming-like embrace of very restrictive measures (two weeks to flatten the curve), that retrospectively provided no value and a great deal of harm.
One that stood out at the time and in retrospect sounds premonitory was Glenn Loury, who in a bloggingheads.tv discussion with in the Spring of 2020 raised this very question
The countries that locked down to eradicate the virus (New Zealand, Australia, Taiwan) did considerably better than those who merely flattened the curve… over… and over… again… (Italy, US, UK, Germany, etc), but these did better than those who pretended nothing’s happening (Iran, Bulgaria).
“The Postal Service delivers about 130 billion pieces of mail over a year to 163 million customers,” said Paul Shade with the U.S.P.S. “It still remains the most secure way to transmit anything from any type of mailing.”
Shade said he is confident the security works.
“They really don’t need to feel nervous about sending you the check,” said Shade.
Shade said to protect your mail, drop it off at the post office or their blue boxes.
“When you’re utilizing the blue boxes, it’s also imperative to check the time that that is going to be picked up,” said Shade. “You don’t want that mail sitting in any place overnight.”
He said the same goes for your home mailbox. Never leave mail out for too long. Shade said you can even have them hold your mail by visiting their website.